Innovative armor — exploring ThreatDown’s impact on cyber defense
The modern digital landscape has hackers who constantly evolve their tactics, so a focus on cyber defense becomes paramount. When cyber threats loom large, businesses and individuals must remain vigilant against the ever-present danger of malware. Given the greater importance of cybersecurity as a priority for online ventures big and small, companies like Malwarebytes are leading the fight against malicious software.
Staying at the forefront of innovation, Malwarebytes' ThreatDown is not your typical cybersecurity tool. It's a unique solution that takes a comprehensive approach to threat intelligence and mitigation. Unlike traditional cybersecurity solutions, ThreatDown is designed to proactively identify, analyze, and neutralize emerging and existing threats across various vectors, making it a standout innovation in the fight against malware.
An overview of ThreatDown with its game-changing cyber defense features
At its core, ThreatDown harnesses the power of cutting-edge technologies, including machine learning, behavioral analysis, and real-time threat intelligence, to provide users with unparalleled protection against malware attacks. By continuously monitoring for suspicious activities and anomalies, ThreatDown can swiftly detect and respond to threats before they can inflict damage.
One of ThreatDown's key features is its emphasis on threat intelligence sharing and collaboration. Malwarebytes leverages its vast network of sensors and endpoints deployed worldwide to gather valuable insights into the latest malware trends and attack vectors. This collective intelligence is then fed into ThreatDown's advanced analytics engine, enabling it to precisely identify emerging threats and patterns.
Furthermore, ThreatDown goes beyond traditional signature-based detection methods by employing heuristic analysis and behavioral monitoring techniques. This methodology enables it to detect previously unknown threats and zero-day exploits that may evade detection by conventional antivirus software.
Why is being proactive with your cyber defenses so essential in the context of today's internet?
ThreatDown's proactive approach to threat mitigation is a game-changer. Instead of waiting for malware to strike and then reacting, ThreatDown takes preemptive measures to block, quarantine, or neutralize potential threats. This approach minimizes the risk of data breaches and system compromises and helps organizations maintain operational continuity and safeguard their reputation, significantly boosting their cybersecurity posture.
Moreover, ThreatDown offers seamless integration with existing security infrastructure, allowing organizations to augment their defenses without disrupting workflows or introducing complexity. Whether deployed as a standalone solution or integrated into a comprehensive cybersecurity stack, ThreatDown enhances overall resilience against malware and other cyber threats.
ThreatDown is not just a product, but a comprehensive solution backed by Malwarebytes' cybersecurity experts. These professionals provide round-the-clock support and guidance to users, ensuring organizations have the resources and expertise to stay ahead of evolving threats. From threat analysis and incident response to best practice recommendations and security updates, Malwarebytes' dedicated professionals support you every step of the way.
More about the ThreatDown Endpoint Detection & Response (EDR) functionality
The ThreatDown EDR functionality includes immediate response capabilities, such as isolating infected systems. It also offers comprehensive remediation to restore affected endpoints. Some of the features include ransomware rollback, attack isolation at multiple levels, and a lightweight deployment to keep performance optimal. Read more on the EDR datasheet from Malwarebytes:
"ThreatDown EDR includes high-powered tools and customizable options that users can embrace as their skill level grows and the organization’s security needs change. By deploying our readily accessible cloud-based security platform, organizations of all sizes gain powerful detection and remediation while freeing their security teams to spend time on other more pressing projects.
ThreatDown EDR helps prevent cyber threats—including malware, brute force attacks, and zero-day exploits—from reaching your environment. To do so, it continuously searches for known malware using rules-based threat detection while proactively hunting for unknown malware using AI-based (also known as “behavioral-based”) detection designed to detect and analyze anomalous files and programs to mitigate risk. Whether known or unknown, detected threats trigger alerts that include the details users need to respond quickly and appropriately."
The source of this quote is the EDR datasheet from Malwarebytes, which can be found on the www.threatdown.com/products/endpoint-detection-and-response/ page.
A preview of the OneView portal for ThreatDown users
ThreatDown users benefit from a wealth of support materials and blog posts useful for learning how best to protect their digital assets:
Of course, the core system that the customers will use for managing the ThreatDown platform after implementation is the OneView portal:
This portal is where users can fine-tune — in great detail with much control — their specific configuration:
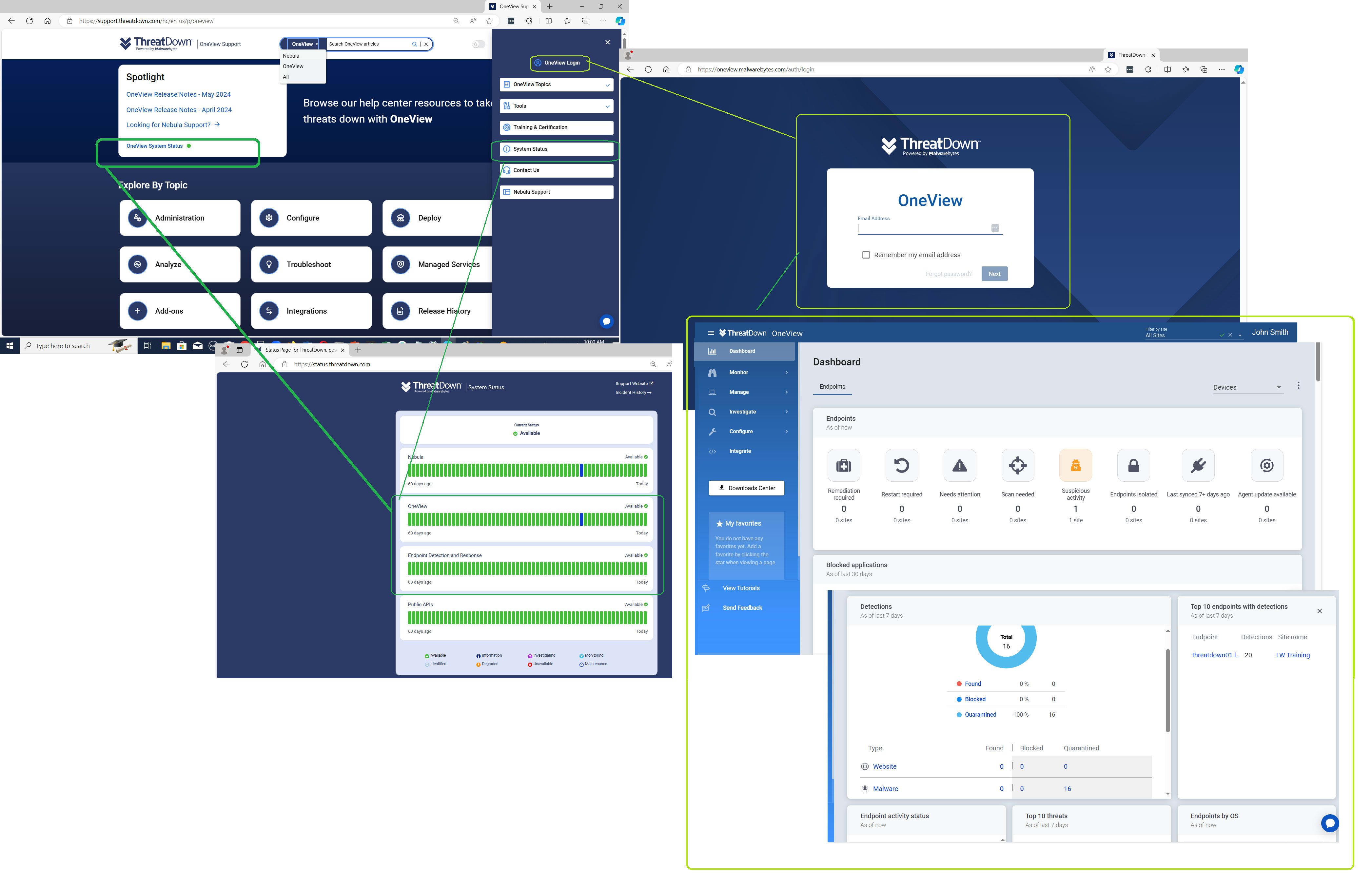
Threat metrics can be reviewed and analyzed here, among the rich set of features provided:
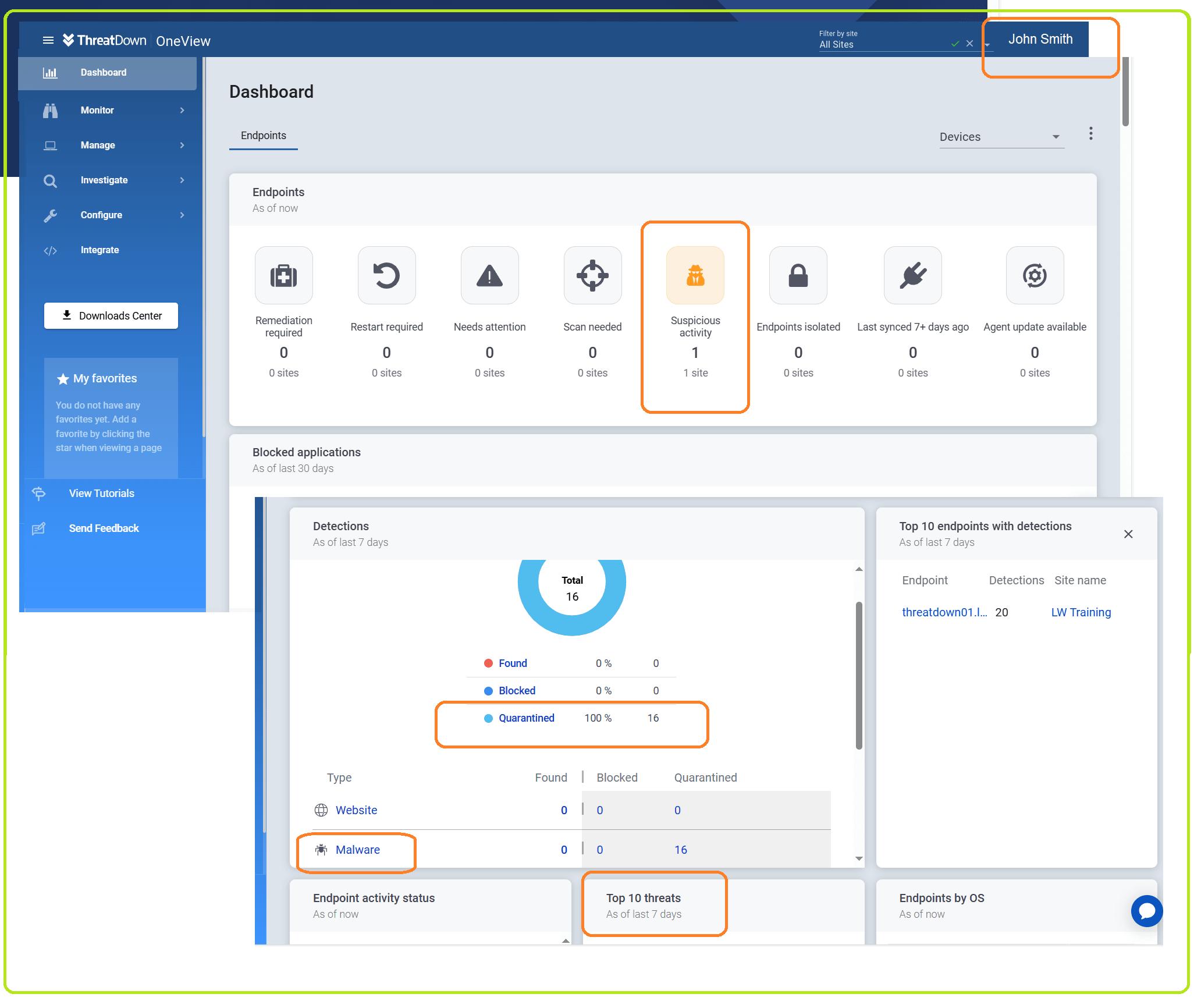
Summing up the enhanced cyber defense stance that ThreadDown represents
ThreatDown represents a paradigm shift in cyber defense, empowering companies to take a fortified position in the battle against malware and other forms of cyberattack. Indeed, this next generation web infrastructure and server protection scheme leverages advanced technologies, threat intelligence sharing, and proactive mitigation strategies to build a more sophisticated "force field" for deterring cybercriminals.
ThreatDown equips users with what they need to prevent dangerous actors operating in a dynamic threat landscape. In a time where cyber threats change by the day, solutions like ThreatDown safeguard online assets and maintain trust in a robustly connected world.
Related Articles:

About the Author: Luke Cavanagh
Product Operations Manager at Liquid Web. Devoted husband and Tween wrangler. Synthwave enthusiast. Jerry Goldsmith fan. Doctor Who fan and related gubbins.
Our Sales and Support teams are available 24 hours by phone or e-mail to assist.
Latest Articles
How to install PyTorch on Linux (AlmaLinux)
Read ArticleInnovative armor — exploring ThreatDown’s impact on cyber defense
Read ArticleControlling PHP settings with a custom php.ini file
Read ArticleLinux dos2unix command syntax — removing hidden Windows characters from files
Read ArticleChange cPanel password from WebHost Manager (WHM)
Read Article


